Table of contents
- Creation of Coins
- Transactions and double spending
- LifeCycle of transactions
- The Solution to Double Spending.
- BitCoin Scripts
- BitCoin Peer-to-Peer Network
- Transaction in Bitcoin Network
- Asymmetric encryption and how it works in Blockchain.
- Block Mining
- Block propagation and block relay
- Working with Consensus in BitCoin
- Proof of Work (PoW)
Creation of Coins
The creation of Bitcoin can be traced back to a whitepaper published in 2008 by an unknown person or group of people under the pseudonym Satoshi Nakamoto. The whitepaper, titled "Bitcoin: A Peer-to-Peer Electronic Cash System," proposed a decentralized digital currency that would allow for secure, anonymous transactions without the need for intermediaries like banks or payment processors.
To bring this vision to life, Nakamoto developed the first implementation of the Bitcoin software and released it in January 2009. The software, which is open-source and freely available, allows users to send and receive bitcoins over the internet.
The creation of new bitcoins is achieved through a process known as mining. Mining is the process of using computational power to solve complex mathematical problems, and when a miner solves a problem, they are rewarded with a certain amount of bitcoins. This process is designed to be resource-intensive and difficult, so it is not possible for any single person or group to control the creation of new bitcoins.
The total number of bitcoins that can be created is limited to 21 million, with the final bitcoin set to be mined in the year 2140. This fixed limit on the supply of bitcoins is intended to prevent inflation and ensure that the currency retains its value over time
Transactions and double spending
Transactions in Blockchain are building blocks of Blockchain ( I mean literally). Each Blockchain is made up of several transactions.
LifeCycle of transactions
Let's Imagine you need to send some Bitcoin to your friend Alice, once you click on the send money than that transaction is got broadcasted to all the Miners out there and miners validate the transaction through several methods(We will talk about them later in this article) on successfully validating the transaction, if more than 50% agrees that block is added to the Blockchain.

Now, let's assume Buyer wants to send some money to Alice and Bob not that he only has 15$ worth of Bitcoin. He made two transactions one for 11$ and one for 6$ if a miner validates and tries to validate it, both can see the current balance in Buyer is 15$ hence in this case if transactions are approved Buyer will be sending more money than it originally had. This is called the Double spending Problem.
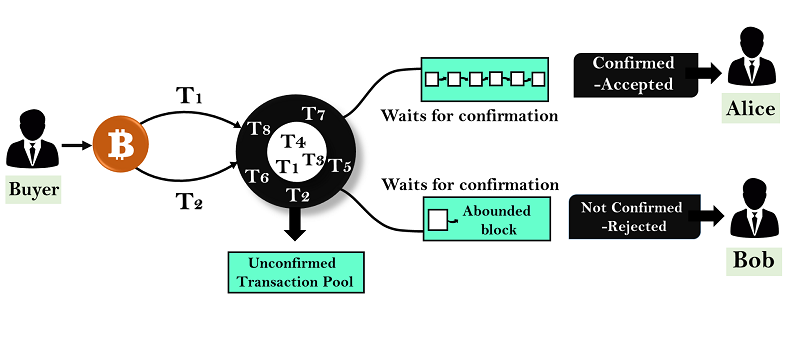
The Solution to Double Spending.
When a transaction is made on the Bitcoin network, it is broadcast to all nodes in the network. Each node verifies that the transaction is valid by checking that the sender has sufficient funds and that the transaction has not already been spent.
Once the transaction is verified, it is bundled together with other transactions into a block. Miners compete to solve a cryptographic puzzle related to the block, and the first miner to solve the puzzle and add the block to the blockchain is rewarded with newly minted bitcoins.
Once a block is added to the blockchain, it cannot be altered, so any double-spending attempts would be rejected by the network. In order for an attacker to successfully double-spend, they would need to control the majority of the computing power on the network, which is extremely difficult and expensive to do in practice.
BitCoin Scripts
If I have to explain this in simple words "Bitcoin scripts are language Bitcoin uses to do everything it can. from sending funds from a wallet to allowing the creation of multi-user accounts."
Bitcoin Script is not a fully fledge programming language meaning it has some limitations and runs in a specific environment, However, this limitation is intentional as this prevents infinite or endless looping and error execution. Where malicious parts of the program can be free to create complicated operations to consume the rate of hash and slow down the Bitcoin system through infinite loops.
A Bitcoin script uses the LIFO pattern to read the instruction, it runs from Left to Right executing commands/instruction one by one. To implement this kind of functionality a popular data structure Stack is used.
To learn more about Bitcoin Script you can refer to this amazing article here.
BitCoin Peer-to-Peer Network
Before I explain to you how BitCoin Peer to Peer Network works let me first explain what Peer to Peer network is.
A Peer to Peer network does not need a server to send data to other members of the network. Let's take an example you want to send a movie from your local device to your friend's device. Now there is one way to establish a server from which both you and your friend connect so that you can upload the movie to the server and your friend can download it from the server itself. Now another way is to directly send the movie to your friend without the intervention of any server, this can be achieved using a peer-to-peer model where you and your friend both are peers. And once you invite a couple of your friends, it becomes a network of peers.

If I have to define it goes something like this, A peer-to-peer network is one in which two or more PCs share files and access devices such as printers without requiring a separate server computer or server software.
Now, that we are clear about the Peer-to-Peer network let's look at how blockchain uses this to establish a secure and decentralized network.
A Blockchain has nodes that are peers in the Peer-to-Peer network, each node in the blockchain are miner which has the capability to add a new block to the chain. So, every time transaction happens in Blockchain it gets broadcasted to these nodes, now each node races to validate this transaction, and then once the transaction is validated, this transaction then added to Blockchain. After 51% of nodes agree on this is considered as the Main Blockchain. In this manner, Blockchain achieved pure decentralization and security.
Transaction in Bitcoin Network
Let's again take Alice and Bob's example and understand the transaction in-depth and how every transaction is protected.
But before that let us look at the concept of asymmetric encryption.
Asymmetric encryption and how it works in Blockchain.
Now, to understand this let's first understand how symmetric encryption works. Suppose Bob wants to send some data to Alice but the data is sensitive and Bob wants to send this in a way that only Alice can read it. Alice will send her the box so that Bob can put the data in the box and close it. Once the box is closed only Alice can open the Box with her key, let's call this key Alice's Private key.
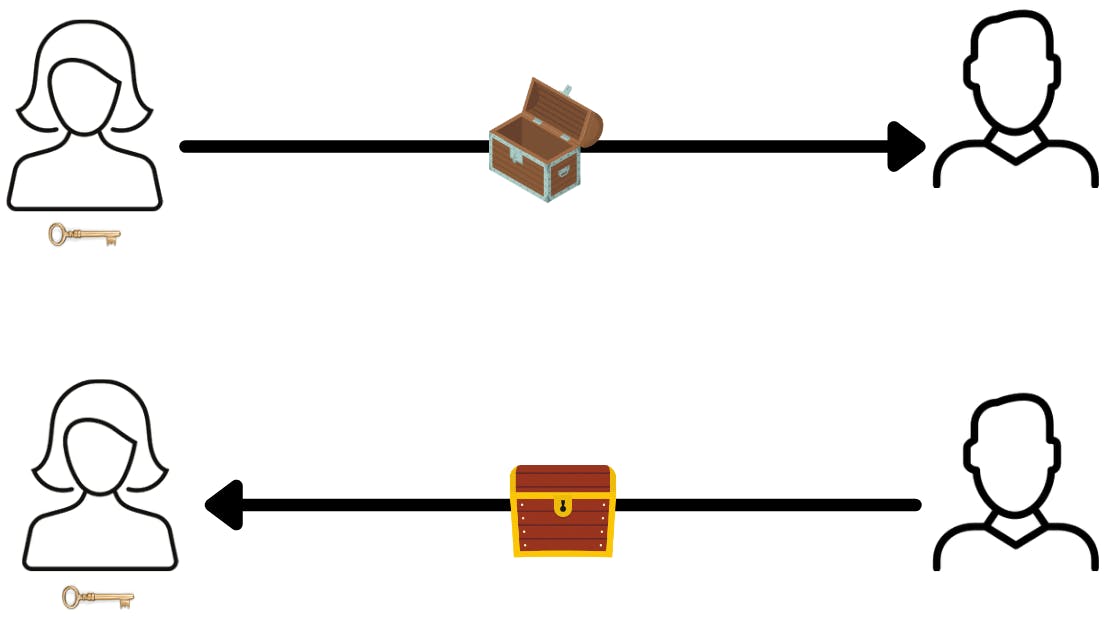
Now in cryptography, the same concept is happening, to send a message to Alice Bob encrypts the data using the Hash function such that only Alice's private key can Hash it back to the original data.
The problem with the above method was for every time Alice wants to receive a message Alice have to create numerous keys and boxes to receive messages from numerous people. This can be really problematic and hence the concept of the Asymmetric key was introduced.
Now in the Asymmetric Encryption key, Alice has two keys one is called Alice's private key, and the other is called Alice's Public key. Now the public key is shareable and the private key must not be disclosed.
Now, every time someone wants to send a message to Alice they can use Alice's public key and send it to Alice now that message can only be decrypted by Alice's private key.
The math behind is quite long so we will discuss it in later articles, but for now, we understood the private and public key concepts. Let's see how it is implied in Blockchain
In Blockchain when Alice wants to send money to BOB that data will be sent to the miner where they verify some conditions like the following.
Does Alice have enough money?
Does Alice is the one who sent the money to Bob or is it someone else?
For checking the available balance in the wallet BTC uses something called UTXO. An overview on UTXO will be that it is a set of all the previous transaction done by Alice and after adding and subtracting everything if the balance matches then the miner approve the transaction.
And to verify if the transaction came from Alice something called a Digital signature is used where Alice signs with her private key and sends it to the miner with other data. Well, you have to understand that those logics are automatically implemented in the wallet and Alice doesn't actually sign anything. Moving on what kind of data is sent to the miner?
Well, the data might look something like this with other data of course
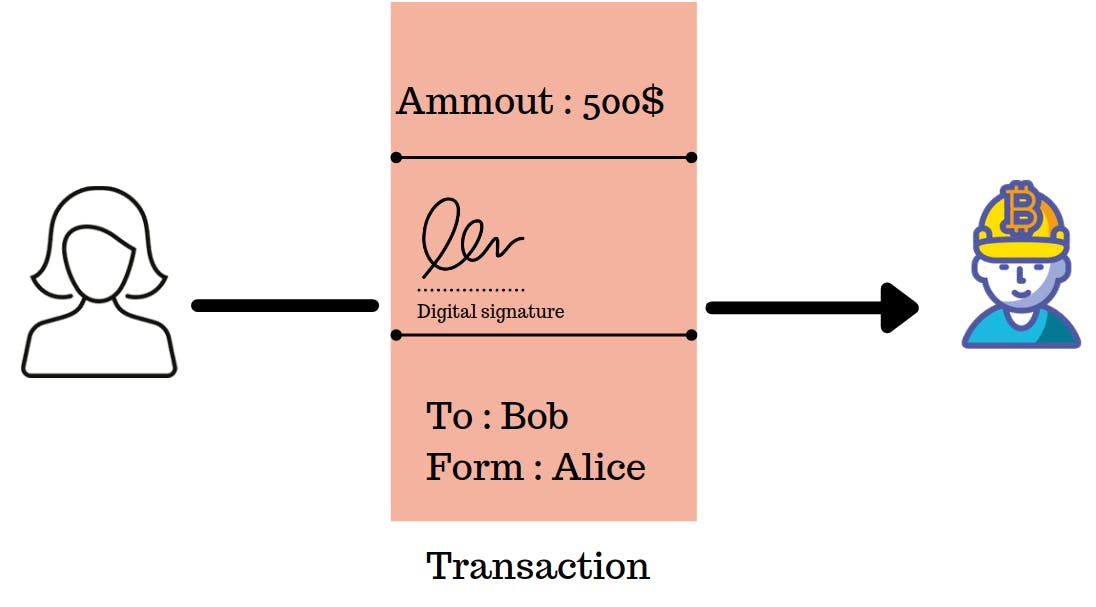
Once it is received the miner will validate the transaction and add it to the Blockchain. Once added to Blockchain the data becomes immutable.
Block Mining
Well, till now it's clear that the blockchain is made of a number of blocks. So what are these blocks and which kind of data do they contain?
Well if we see an overview block looks something like the below.
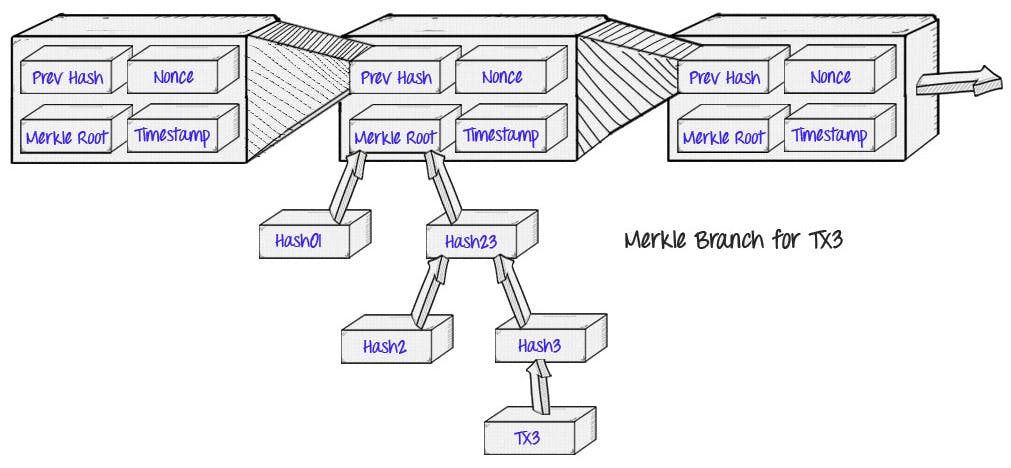
In this, we can see that a single block contain
Previous Hash
Nonce
TimeStamp
Merkel Root.
But in exactly a block look something like this with a lot of data
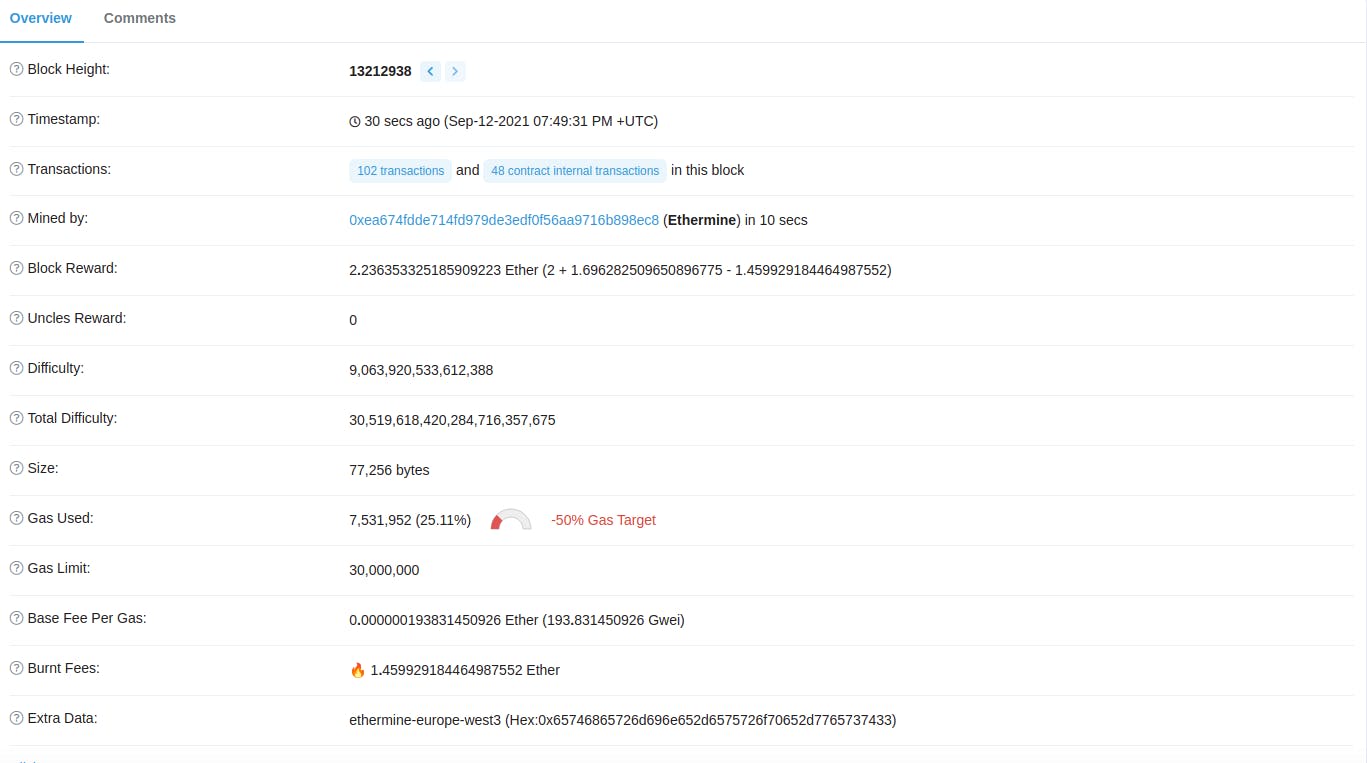
You can see all the transactions and blocks of the public Blockchain. Here I used Etherscan to get the block data but there are a lot of services out there.
So what happens is every time transactions are made they came to miners where miners validate the transactions and then try to add that block to the public Blockchain.
Why I used "try to add"? Instead of adding, well every miner is trying to add a new block to the Blockchain continuously all the time and it's like a race between every miner.
The way blockchain validates whether a block is valid or not is called Consensus Mechanism. There are different ways the Consensus Mechanism works one which is very popular is Proof of Work others are Proof of Stake***,*** Proof of Capacity***, and*** Proof of Activity.
In this article, we will only talk about the Proof of Work.
In Proof of Work, every miner has to compute a hash value for the block in some given condition.
Let's say you are a miner and you have to calculate a hash value that should start with 4 0's
for example 0000x147a9393258780beef7d
to calculate something like this takes a lot of trial and error and a lot of computational power. And also there is only one thing you can change in the block which is the value of Nonce.
So every time you want a new hash value, you keep incrementing the value of Nonce and by finding a valid hash you can add that hash to the block.
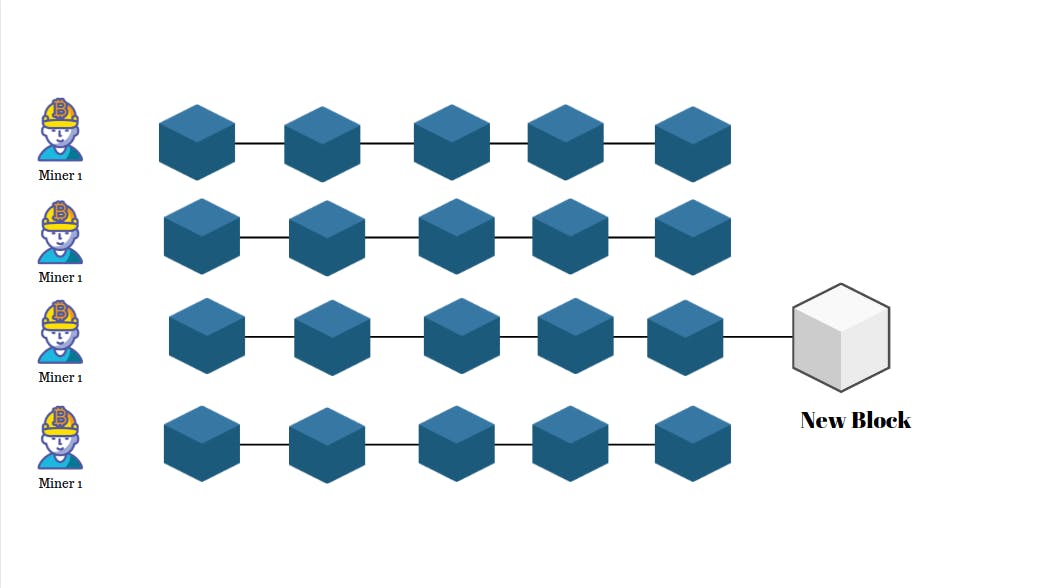
Well if any miner can add to the Blockchain isn't that make the Blockchain untrustable and unsafe?
Well here comes the power of Decentralization to save you. Every time a miner adds a block to the Blockchain other miners do a validation check on that block. If the block is valid and matches their own version of the Blockchain if everything is valid they add that Blockchain to their own version of the Blockchain and start mining the new block.
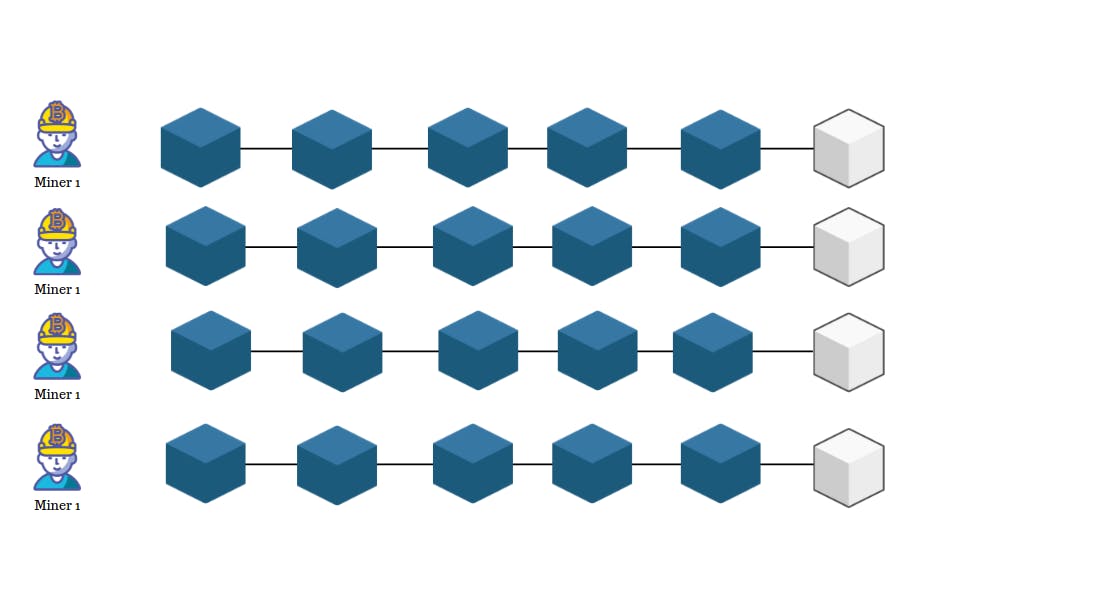
Say, if some malicious group tries to add an invalid block to the Blockchain for their own profile. After successfully mining the Blockchain their block will be rejected by other miners which can cost them a lot of money and computation power.
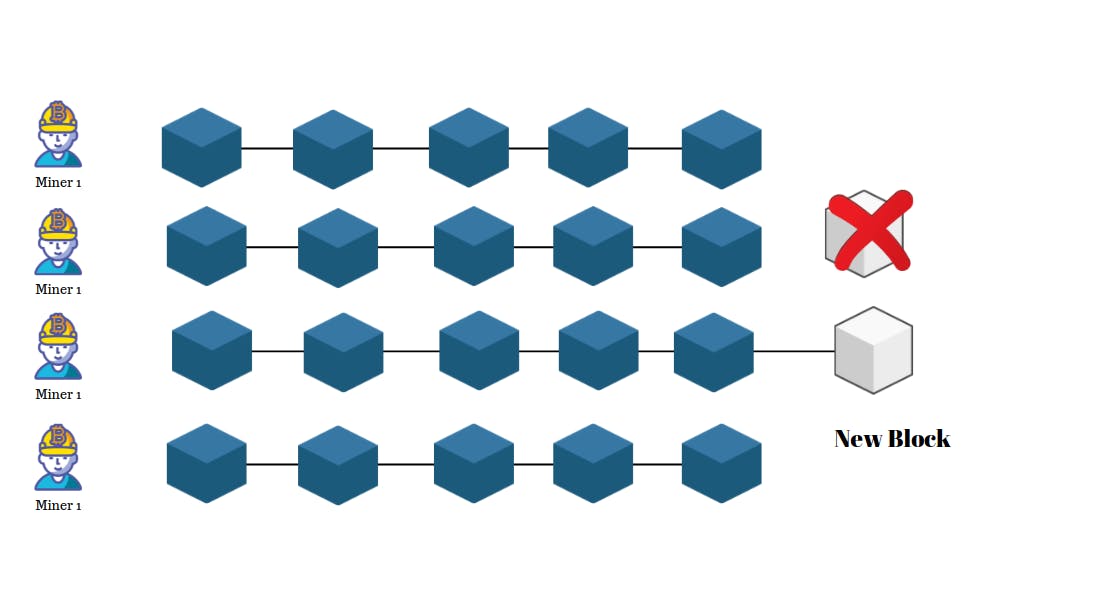
If another miner successfully mines a valid block the whole Blockchain will move to that version of the block and malicious manners have to sync up to mine the next block.
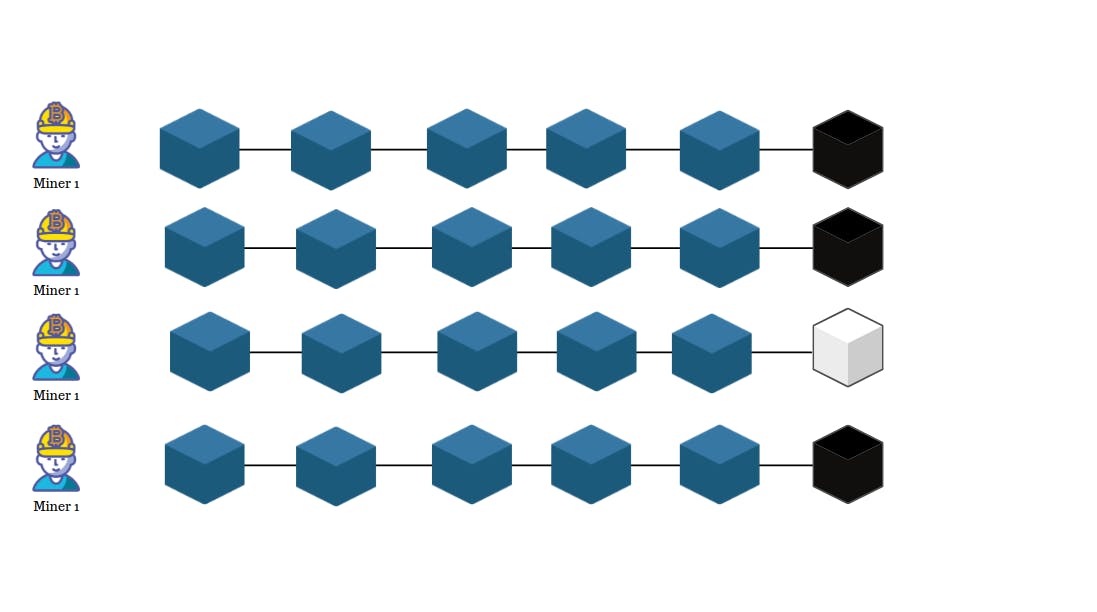
Well, for every successful mining, each miner is given some reward. For mining on BTC Blockchain, it's BTC coin and on mining on ethereum Blockchain, it's ethereum.
fun fact: It's the only time a new coin is created. (It's just an analogy)
Block propagation and block relay
Once a block has been mined, it must be propagated to the rest of the network to ensure that all nodes have a complete and up-to-date copy of the blockchain. This is done through a process called block relay, in which the newly mined block is broadcast to other nodes in the network. As explained above.
Working with Consensus in BitCoin
Consensus is the mechanism by which the Bitcoin network ensures that all transactions are valid and secure. This is done through a process called proof of work, which we will explore in more detail in the next section.
Distributed Consensus in open environments
Distributed consensus in open environments like Bitcoin refers to the process of reaching a common agreement among a network of independent nodes without the need for a centralized authority. In Bitcoin, this consensus mechanism is achieved through a process known as mining, in which nodes compete to solve a cryptographic puzzle and add a new block of transactions to the blockchain.
Each node in the Bitcoin network maintains a copy of the blockchain, which contains a record of all transactions that have ever taken place on the network. When a new transaction is initiated, it is broadcast to all nodes on the network. The nodes then verify the transaction by checking that the sender has sufficient funds and that the transaction meets all other necessary criteria. If the transaction is deemed valid, the node adds it to its copy of the blockchain and broadcasts the updated blockchain to the rest of the network.
In order for the network to reach a consensus on the validity of each transaction, all nodes must agree on the current state of the blockchain. This is achieved through the mining process, in which nodes compete to solve a cryptographic puzzle and add a new block of transactions to the blockchain. The first node to solve the puzzle and add a new block to the blockchain is rewarded with newly created bitcoins and transaction fees.
Once a new block has been added to the blockchain, all nodes on the network must update their copy of the blockchain to reflect the new state. This process is called block propagation and block relay, and it is essential for maintaining the consistency and integrity of the network.
The distributed consensus mechanism used in Bitcoin is designed to be resistant to attacks and manipulation. In order for an attacker to successfully manipulate the network, they would need to control a majority of the network's computational power, a scenario known as a 51% attack. This is difficult to achieve due to the high cost and computational resources required to successfully carry out such an attack.
Proof of Work (PoW)
Introduction
Proof of work is a consensus mechanism that was first introduced in Bitcoin and is now used by many other cryptocurrencies. The basic idea is that miners must solve a cryptographic puzzle to create a new block, and the first miner to do so is rewarded with newly created bitcoins. This incentivizes miners to secure the network and makes it difficult for any one entity to control the network.
Hash Cash PoW
HashCash, a proof-of-work algorithm, was designed by Adam Back in 1997 to prevent email spam and denial-of-service attacks. HashCash is now also being used in Bitcoin mining.
How HashCash Works
HashCash is a proof-of-work algorithm that requires a certain amount of computational work to compute. For email use, a textual encoding of a HashCash stamp is added to the header of an email. This stamp serves as proof that the sender has expended a modest amount of CPU time calculating the stamp prior to sending the email. The Hashcash stamp adds extra verification for emails and makes it unlikely that the email is being sent by a spammer. The receiver can verify the stamp at a negligible computational cost.
The Technical Details
The header contains the Hashcash format version, the number of partial preimage bits in the hashed code (known as the "bits"), the date that the message was sent, the resource data string being transmitted (such as an email or IP address), and a string of random characters encoded in base64 format. Additionally, the header contains information proving that the required computation has been performed. The recipient verifies the authenticity of the Hashcash stamp via checks including calculating the 160-bit SHA1 hash of the entire string and checking the date of the message to make sure it was sent recently. The recipient also ensures that the email address in the hash string matches any to which the recipient subscribes.
Implementation and Advantages/Disadvantages
HashCash is simple to implement and doesn't require real money, which is advantageous over micropayment proposals. However, it requires computational resources and is thus less accessible from low-end systems. As computers continue to get faster, the difficulty of the calculations required must be increased over time. HashCash can be incrementally deployed, so it can be adopted without a large upfront investment.
Applications
HashCash is used for false positives in automated spam filtering systems and as a means to slow down comment spam in blogs. It has also been implemented in the Mozilla Thunderbird email client and in Microsoft's Coordinated Spam Reduction initiative.
Overall, HashCash has been effective in combating email spam and denial-of-service attacks and continues to be a valuable tool in the fight against online threats.
Bitcoin PoW
Proof of Work (PoW) is a consensus mechanism used by the Bitcoin network to confirm transactions and add new blocks to the blockchain. It is a computationally intensive process that involves solving a complex mathematical problem called a cryptographic puzzle. The first node to solve the puzzle is rewarded with newly created bitcoins and transaction fees and is responsible for adding a new block of transactions to the blockchain.
The cryptographic puzzle used in Bitcoin's PoW mechanism is called the SHA-256 algorithm. The algorithm takes an input and produces a fixed-length output, known as a hash. The challenge for miners is to find a hash that meets a specific set of criteria, known as the target. This target is set by the network difficulty, which is adjusted every 2016 block to maintain a target block time of 10 minutes.
To solve the cryptographic puzzle, miners use specialized hardware, known as Application-Specific Integrated Circuits (ASICs), to perform billions of hash calculations per second. This process is known as mining, and it requires a significant amount of computational power and energy.
Once a miner solves the cryptographic puzzle and finds a hash that meets the target, they broadcast the new block to the network. Other nodes on the network then verify the block by checking that the transactions included in the block are valid and that the hash meets the target criteria. If the block is deemed valid, it is added to the blockchain, and the miner is rewarded with newly created bitcoins and transaction fees.
One of the benefits of Bitcoin's PoW mechanism is that it is designed to be decentralized, with no central authority controlling the mining process. Any node on the network can become a miner and participate in the mining process, provided they have the necessary hardware and energy resources.
However, there are also some drawbacks to Bitcoin's PoW mechanism. The energy-intensive nature of mining has led to concerns about the environmental impact of the Bitcoin network, with some estimates suggesting that the network consumes as much energy as a small country. Additionally, the increasing difficulty of mining and the centralization of mining pools have made it difficult for individual miners to compete and earn rewards.
Attacks on Pow and monopoly problems
While Bitcoin's Proof of Work (PoW) consensus mechanism is designed to be secure, it is still vulnerable to certain types of attacks. One such attack is known as a 51% attack, in which a single entity or group of entities controls more than 50% of the network's computational power. This would give the attacker the ability to manipulate the network by altering transactions, double-spending bitcoins, and blocking or censoring transactions.
A 51% attack is difficult to carry out in practice, as it requires a significant amount of computational power and energy resources. However, it is not impossible, and there have been several instances of smaller blockchains suffering from 51% attacks. In 2018, the cryptocurrency Verge suffered multiple 51% attacks, leading to losses of over $1 million.
Another issue with Bitcoin's PoW mechanism is the centralization of mining pools. Mining pools are groups of miners who combine their computational power and share the rewards of mining. While mining pools are beneficial for individual miners who may not have the resources to mine on their own, they can also lead to centralization and the potential for monopolies.
As mining becomes increasingly difficult and expensive, small-scale miners may drop out, leaving larger mining pools with a greater share of the computational power. This can lead to a situation where a small number of mining pools control the majority of the network's computational power, leading to concerns about centralization and the potential for monopolies.
To illustrate this issue, we can look at the distribution of Bitcoin's computational power, known as the Hashrate. As of March 2023, the top three mining pools control over 50% of the Hashrate, with the largest pool, F2Pool, controlling over 20%.
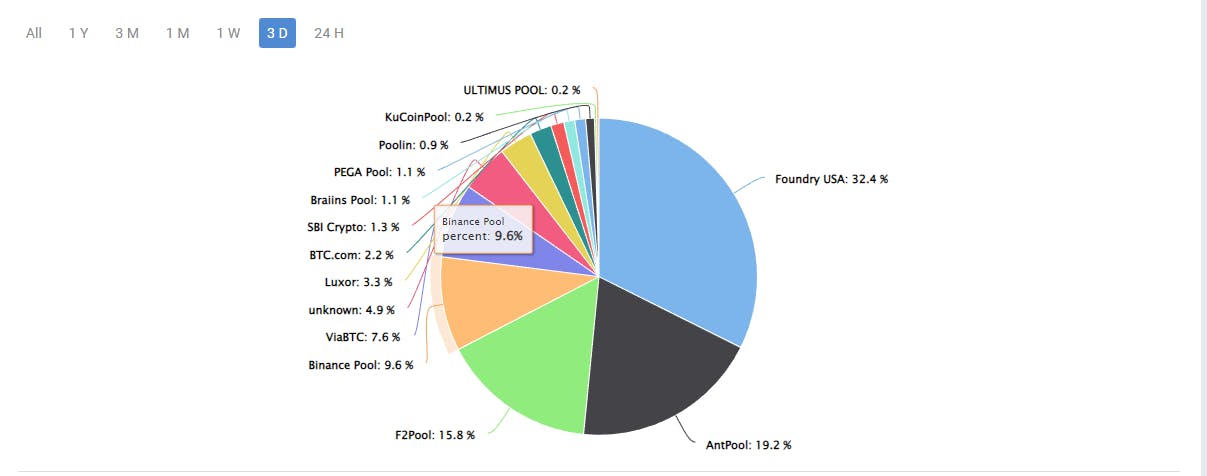
While this distribution is not necessarily a cause for concern, it does highlight the potential for centralization and the need for continued efforts to decentralize the mining process.
Proof of Stake:
Proof of stake is an alternative consensus mechanism that is gaining popularity in the cryptocurrency world. Rather than relying on computational power to secure the network, proof of stake requires users to hold a certain amount of the cryptocurrency to participate in the network's consensus process. This incentivizes users to hold and use the cryptocurrency, rather than simply mining it for profit.
Proof of Burn and Proof of Elapsed Time
Proof of burn and proof of elapsed time are two other alternative consensus mechanisms that have been proposed. Proof of burn involves burning or destroying coins to demonstrate commitment to the network, while proof of elapsed time involves randomly selecting a validator based on the amount of time they have been participating in the network.
The Life of a Bitcoin Miner
Bitcoin mining is a competitive and constantly evolving industry, with miners competing to earn newly created bitcoins and secure the network. To be successful, miners must have access to specialized hardware and software, as well as a reliable source of electricity to power their operations. The profitability of mining can fluctuate depending on a variety of factors, including the price of bitcoin, the difficulty of mining, and the cost of electricity.
Mining Difficulty
Mining difficulty is a measure of how difficult it is to find a valid hash for a new block in the Bitcoin network. As more miners join the network and more computational power is added, the difficulty of mining increases to maintain a consistent rate of block creation.
Mining Pool
Mining pools are groups of miners who pool their computational resources together to increase their chances of earning new bitcoins. Pools allow miners to share the rewards for mining new blocks, making it more accessible to smaller-scale miners who may not have the resources to mine on their own.
Conclusion
In conclusion, Bitcoin is a complex and constantly evolving network that relies on a variety of technologies and mechanisms to ensure its security and resilience. From the creation of coins through mining to the consensus mechanisms used to verify transactions, each aspect of the network plays an important role in its success. As the cryptocurrency industry continues to grow and evolve, it will be interesting to see how these technologies and mechanisms continue to develop and adapt to new challenges and opportunities.

