
Demystifying Blockchain: Understanding its Inner Workings and Security Aspects"
Introduction: Overview of Blockchain
Blockchain promises to fundamentally solve the issues of time and trust to address inefficiencies in industries such as financial, healthcare, supply chain, logistics, etc. Blockchain's key features include data immutability and a shared ledger where transactional updates are performed by a consensus-driven trust system.
With the blockchain system design, we are attempting to build a system that implied trust. This trust system leads to reduced risks, and various applied technology constructs sucha as cryptography, smart contracts, and concesus essentially create gates to not only reduce risk but to also infuse added security into the transaction system.
What are Public Ledgers
A public ledger is a way to keep all the transactions on a particular blockchain open and accessible to the public. This provides transparency and openness, though it is publically available and accessible to the general public this ledger is immutable i.e can't be modified.
Here are some of the examples from the Ethereum Blockchain
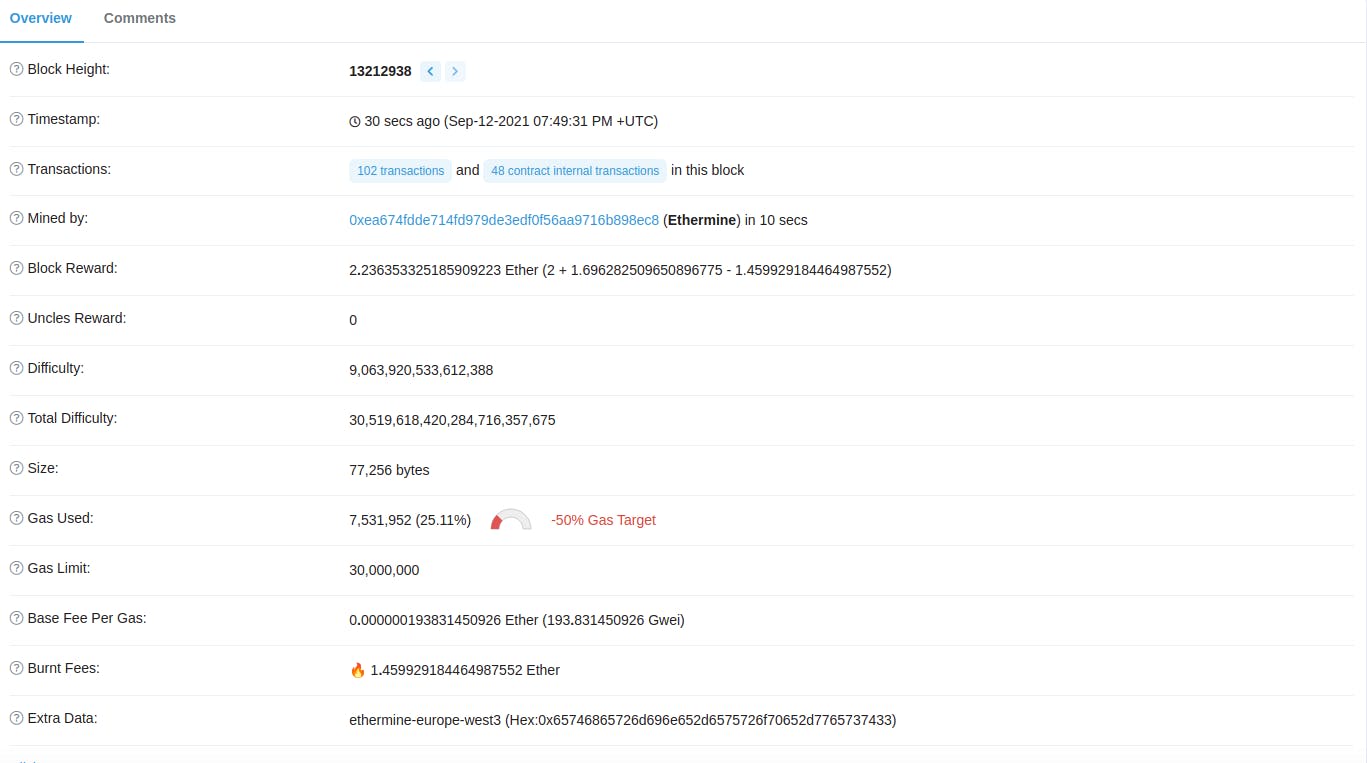
Business Logic with Smart Contact
Smart contracts are business logic that is stored on the blockchain (hence immutable) that runs when predetermined conditions are met. They typically are used to automate the execution of an agreement so that all participants can immediately be certain of the outcome, without any intermediary's involvement or time loss.
Some benefits of using a Smart Contract
Speed, efficiency, and Accuracy: Once the conditions are met smart contracts are executed immediately as they are digital and automated, and there's no paperwork to process or filling/refilling documents which can lead to human errors.
Trust and Transparency: Smart Contract establishes trust as there is no third party involved and once Smart Contracts are deployed it's immutable meaning no one can change the conditions of the contract.
Security: Blockchain is immutable in nature hence anything deployed on the blockchain is also immutable. On top of the immutability, a Smart contract is highly encrypted and can't be hacked by using current technologies available to humankind.
Savings: Smart contracts are fully automated and hence do not requires any intermediately to handle transactions, which automatically decreases the time and fees associated with them.
How Blockchain Works
I have already written an extensive blog about how blockchain works here. But In case you don't want to read it below is a point-by-point summary.
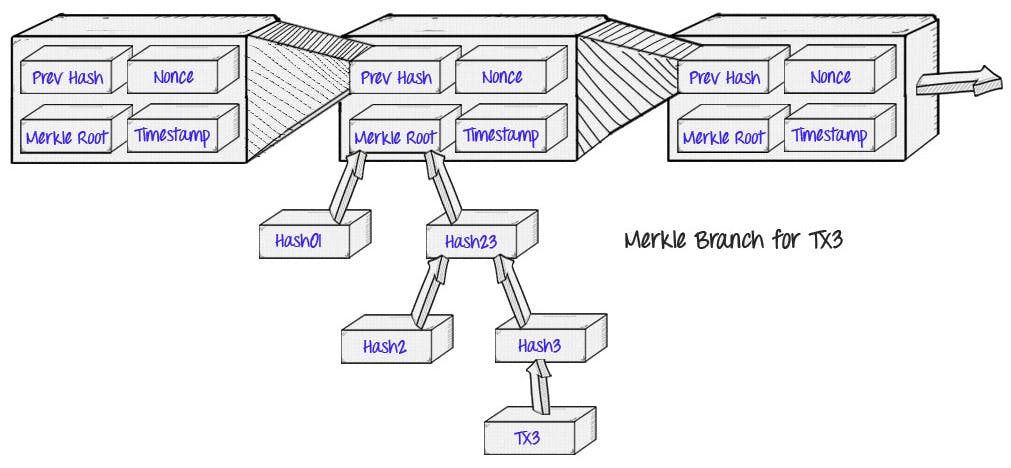
Blocks in Blockchain
A Blockchain is made of smaller chunks of transactions called Blocks. Each transaction creates a new block which is then added to the Blockchain. A block in the blockchain roughly looks like below and has some properties like pevHash, Timestamp, Merkle Root, etc like below. This creates an unbreakable chain of blocks that cannot be altered, ensuring the security and integrity of the data. We will look at Merkle Tree and Hash Pointer later in this article.
Transactions
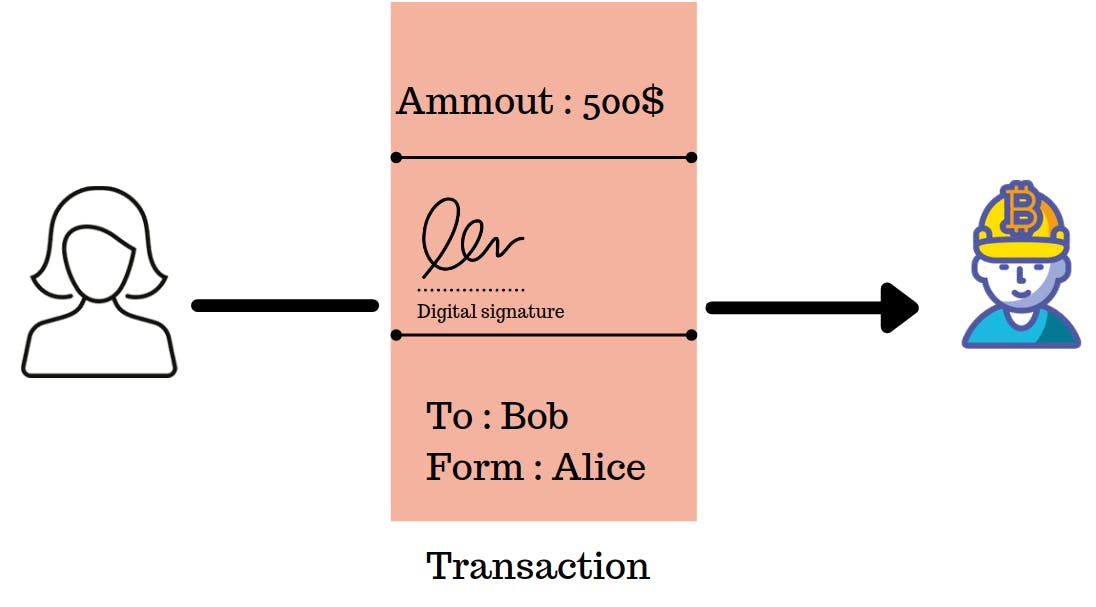
A blockchain transaction is a transfer of value between two parties on a blockchain network. It is a fundamental concept of blockchain technology and is critical to the functioning of any blockchain-based system.
When a transaction occurs on the blockchain, it is validated, verified, and then recorded on the blockchain ledger. Each transaction is recorded as a block on the blockchain network, and these blocks are linked together in a chain using cryptographic hash functions.
This linkage is what makes blockchain immutable and increases security. If a Hacker wants to change the data in Blockchain they have to change the linkage of each block through out the Blockchain network.
Below is a representation of How Transactions work in Blockchain.

Distributed Consensus
With the rise of computers and the Internet, data started to be stored in a distributed way this solved a lot of problems but came with its challenges. One of the challenges we faced was the validation of the data which is added and this needed some consensus algorithms.
In Blockchain we also need a consensus mechanism/ algorithm to validate each transaction to be added to the distributed ledger i.e Blockchain. Famously Proof of Work (POW) is used in blockchains like bitcoin. Ethereum has moved to Proof of Stake (POS) for its consensus mechanism. There are other ways to validate the transaction and once the transaction is validated, it is added to the Blockchain.
Public Vs Private Blockchain
Private Blockchains are also known as permission network similarly Public Blockchain network is known as Permisionless Network. A blockchain supporting a cryptocurrency is public in the sense that anyone can participate without a specific identity. Such blockchains typically use a consensus protocol based on Proof of Work (PoW).
In contrast, permissioned blockchains have evolved as an alternative way to run a blockchain between a group of known, identified participants. A permissioned blockchain provides a way to secure interactions between a group of entities that share a mutual goal but don't fully trust each other, such as businesses that exchange funds, goods, or information. A permissioned blockchain relies on the identities of its peers, and in so doing can use the traditional Byzantine-fault tolerant (BFT) consensus.
To understand more about it you can watch the following video:
Understanding Crypto Currency to Blockchain
A cryptocurrency is a form of digital currency that is secured using cryptography, making it difficult to counterfeit or double-spend. Cryptocurrencies operate independently of a central bank and use a decentralized ledger called a blockchain to record transactions. Blockchain technology uses a distributed network of computers to maintain a secure and transparent record of transactions, which cannot be altered without consensus from the network.
Cryptocurrencies like Bitcoin, Ethereum, and Litecoin are among the most popular examples of cryptocurrencies. Bitcoin, the first cryptocurrency, was created in 2009 by an unknown person or group using the pseudonym Satoshi Nakamoto. Bitcoin and other cryptocurrencies have grown in popularity and are now widely accepted as payment by many merchants.
Permissioned Model of Blockchain
A permissioned blockchain is a type of blockchain that restricts access to authorized users. It is sometimes referred to as a private blockchain, as it is not open to the public. In a permissioned blockchain, participants must be granted permission to view or modify the blockchain data.
Permissioned blockchains are often used by businesses and organizations that require more control over their data. For example, a financial institution might use a permissioned blockchain to manage its records and transactions. This would allow the institution to maintain control over its data while still benefiting from the security and transparency of blockchain technology.
In a permissioned blockchain, the consensus is often achieved through a smaller group of nodes or validators, rather than a larger network of nodes as in a public blockchain. This allows permissioned blockchains to be more efficient, as consensus can be reached more quickly.
Overall, permissioned blockchains offer a way for businesses and organizations to benefit from the security and transparency of blockchain technology while still maintaining control over their data. This makes permissioned blockchains an attractive option for many industries, including finance, healthcare, and supply chain management.
Overview of security aspects of Blockchain
Security is a critical aspect of blockchain technology, as it involves the storage and management of sensitive data. Blockchain technology offers several security measures, including cryptography, consensus mechanisms, and immutability.
Basic Crypto Primitives
Cryptography is a central concept in blockchain technology. It is the science of secure communication in the presence of third parties. Some of the basic crypto primitives used in blockchain technology include:
Cryptographic Hash Function: A cryptographic hash function is a mathematical function that takes input data of arbitrary size and produces a fixed-size output known as a hash. The output is a unique representation of the input data, and even a slight change in the input data will result in a different hash output. This property makes cryptographic hash functions ideal for securing data integrity in blockchain technology.
Digital Signature: A digital signature is a mathematical scheme used to verify the authenticity of digital documents or messages. It is similar to a handwritten signature but uses digital keys instead of a pen. Digital signatures are used to verify the authenticity of blockchain transactions.
Public Key Cryptography: Public key cryptography, also known as asymmetric cryptography, uses a pair of keys (a public key and a private key) to encrypt and decrypt messages. The public key is used to encrypt the message, while the private key is used to decrypt it. Public key cryptography is used to secure blockchain transactions and ensure the privacy and confidentiality of data.
Cryptographic Hash Function
A cryptographic hash function is a mathematical function that takes input data of arbitrary size and produces a fixed-size output known as a hash. The output is a unique representation of the input data, and even a slight change in the input data will result in a different hash output. Cryptographic hash functions are used in blockchain technology to ensure data integrity and security.
Properties of the Hash Function:
The properties of the hash function include:
Deterministic: The same input data will always produce the same hash output.
One-Way: It is computationally infeasible to find the input data from the hash output.
Collision Resistance: It is computationally infeasible to find two different inputs that produce the same hash output.
Fixed Output Length: The hash output is always of a fixed length, regardless of the input data size.
Hash Pointer and Merkle Tree
A hash pointer is a pointer that contains the hash of the data it is pointing to. Hash pointers are used in blockchain technology to link blocks together in a chain. A Merkle tree is a data structure that uses hash pointers to efficiently verify the integrity of large amounts of data. In blockchain technology, Merkle trees are used to verify the integrity of transactions.
Digital Signature
A digital signature is a mathematical scheme used to verify the authenticity of digital documents or messages. It is similar to a handwritten signature but uses digital keys instead of a pen. Digital signatures are used to verify the authenticity of blockchain transactions.
Public Key Cryptography
Public key cryptography, also known as asymmetric cryptography, is a cryptographic technique that uses a pair of keys - a public key and a private key - to encrypt and decrypt messages. The keys are mathematically related, but it is computationally infeasible to derive the private key from the public key.
In public key cryptography, the public key is widely distributed and can be freely shared with anyone who wants to communicate with the owner of the private key. The private key, on the other hand, is kept secret and only known to the owner.
To encrypt a message, the sender uses the recipient's public key to scramble the message, making it unreadable to anyone who intercepts it. The recipient then uses their private key to decrypt the message, making it readable again.
To sign a message, the sender uses their private key to generate a unique digital signature for the message. The recipient can then use the sender's public key to verify the authenticity of the signature and the message.
Public key cryptography has several advantages over symmetric key cryptography, where the same key is used for both encryption and decryption. One of the main advantages is that public key cryptography does not require the exchange of secret keys, which can be a vulnerability in symmetric key cryptography. Another advantage is that public key cryptography allows for digital signatures, which can be used to verify the authenticity of messages and ensure that they have not been tampered with.
Public key cryptography is widely used in blockchain technology to secure transactions and ensure the privacy and confidentiality of data. In a blockchain network, each user has a unique public key and private key pair, which they use to sign and verify transactions. Transactions are broadcast to the network and verified by other nodes using the sender's public key. Once a transaction is verified, it is added to the blockchain and becomes part of the permanent record.
A basic Crypto Currency
A basic cryptocurrency is a digital currency that uses cryptography to secure and verify transactions. Bitcoin is the most well-known cryptocurrency, but there are many others, such as Ethereum, Litecoin, and Ripple. Cryptocurrencies use blockchain technology to create a decentralized, peer-to-peer payment network that is not controlled by any central authority. Cryptocurrencies offer several advantages over traditional currencies, including lower transaction fees, faster processing times, and greater transparency. However, they also present some risks, such as
TL;DR
The article provides an overview of blockchain technology, including its key features and benefits. It explains the concept of public ledgers, smart contracts, and how blockchain works, including blocks, transactions, and distributed consensus. The article also discusses the difference between public and private blockchains, as well as the security aspects of blockchain technology, including basic crypto primitives, cryptographic hash functions, digital signatures, and public key cryptography. Finally, the article provides a brief overview of cryptocurrencies and their advantages and risks.
